Are your GitHub Action PATs exposing your cloud? Learn how exposed secrets lead to breaches and critical steps to secure your CI/CD now.#GitHubSecurity #CloudBreach #DevSecOps
Quick Video Breakdown: This Blog Article
This video clearly explains this blog article.
Even if you don’t have time to read the text, you can quickly grasp the key points through this video. Please check it out!
If you find this video helpful, please follow the YouTube channel “AIMindUpdate,” which delivers daily AI news.
https://www.youtube.com/@AIMindUpdate
Read this article in your native language (10+ supported) 👉
[Read in your language]
Exposed GitHub Secrets: The Hidden Gateway to Cloud Breaches and How to Lock It Down
🎯 Level: Intermediate / Business Leader
👍 Recommended For: DevOps Managers, Cloud Architects, Cybersecurity Professionals
John: In the fast-paced world of enterprise DevOps, one persistent bottleneck has always been balancing speed with security—especially in CI/CD pipelines where tools like GitHub Actions promise automation nirvana. But recent revelations show how exposed Personal Access Tokens (PATs) in GitHub Action Secrets are turning these workflows into direct pipelines for threat actors to infiltrate cloud environments. It’s not just a tech glitch; it’s a business risk that could erode ROI through data breaches and downtime. As a Senior Tech Lead who’s seen pipelines crumble under oversight, I’ll cut through the fluff: this is about engineering reality meeting enterprise stakes. For deeper dives into such threats, tools like Genspark, a next-gen research agent, can help you uncover real-time insights without the noise.
Lila: Hey everyone, Lila here as your bridge for beginners. If you’re new to this, think of GitHub Actions as the automated assembly line in your software factory. Secrets are like the keys to the vault, and PATs are special keys that let you access repos and more. The problem? These keys are getting leaked, opening doors to your cloud setups on AWS, Azure, or wherever. John will go deep, but I’ll keep it grounded—no one gets left behind.
The “Before” State: When Secrets Were Assumed Safe
John: Remember the old days of CI/CD? You’d set up your pipelines with hardcoded credentials or basic env variables, assuming a layer of obscurity kept things secure. Tools like Jenkins or early GitHub Actions felt like a win for speed—deployments in minutes, not hours. But the cost? High vulnerability to insider threats or misconfigurations, with ROI tanking from potential breaches. Fast-forward to now: exposed PATs aren’t just a leak; they’re a highway to your cloud control plane. Contrast that with outdated methods where secrets were siloed but still prone to human error. For visualizing these workflows, check out Gamma to whip up docs and slides that map your “before” vs. “after” states effortlessly.
Lila: Simply put, before these exposures became headline news, teams treated secrets like hidden treasures—buried but not bulletproof. Now, with threats evolving, it’s like leaving your house key under the doormat in a bad neighborhood.
Core Mechanism: How PAT Exposures Lead to Cloud Compromises
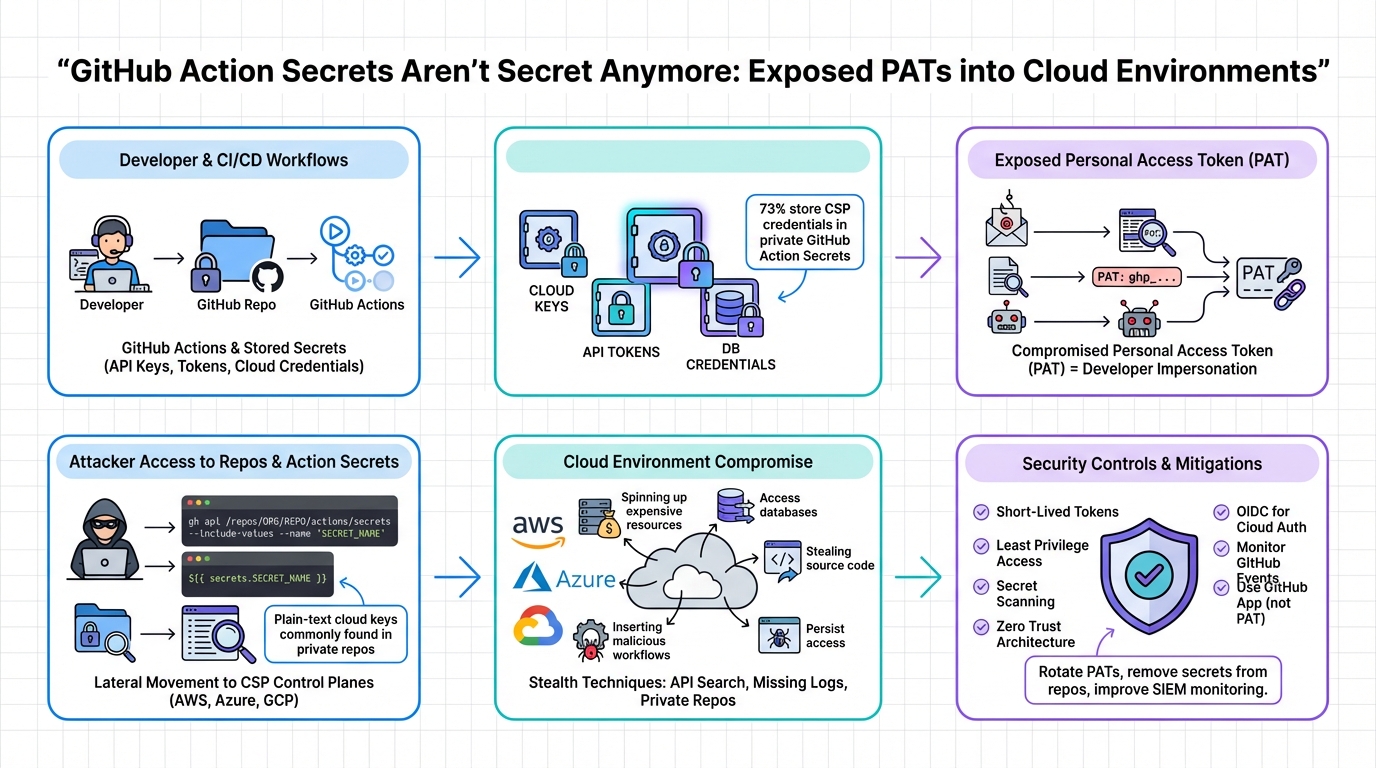
John: Let’s break this down with executive summary logic: GitHub Action Secrets store sensitive data like PATs, which grant access to repositories and, crucially, integrated cloud services. Threat actors exploit these via compromised tokens—often from public repos or supply chain attacks like the Shai-Hulud campaign. Once in, they steal more secrets, inject malicious workflows, and pivot to cloud environments (e.g., AWS via OIDC federation). The engineering reality? No lockfiles or integrity checks in Actions make it a flawed package manager, per industry critiques. To mitigate, adopt OIDC for tokenless auth, pin actions to commits (not tags), and use tools like GitGuardian for scanning. For open-source alternatives, fine-tune models like Llama-3-8B with Hugging Face for custom secret detection pipelines—quantization shrinks it for edge deployment.
Lila: Imagine your PAT as a master key. If stolen, it’s like giving burglars a map to your entire house (cloud). The fix? Better locks and alarms, explained simply.
Use Cases: Real-World Scenarios Where This Hits Hard
John: First, enterprise DevOps: A team deploys via GitHub Actions to AWS. An exposed PAT lets attackers modify workflows, injecting code that exfiltrates S3 buckets—costing millions in breach response. Second, supply chain attacks: Like the tj-actions compromise affecting 23,000 repos, where secrets leak to malicious repos. Third, hybrid cloud setups: PATs bridge GitHub to Azure, enabling lateral movement and ransomware. For video breakdowns, use Revid.ai to create marketing explainers. And for learning secure coding, Nolang is your AI tutor.
Lila: These aren’t hypotheticals—they’re happening now, as per recent Wiz reports.
| Aspect | Old Method (Insecure Secrets Management) | New Solution (Hardened GitHub Actions) |
|---|---|---|
| Token Handling | Long-lived PATs stored plainly, prone to leaks | OIDC for short-lived tokens, no storage needed |
| Risk of Exposure | High—public repos and no integrity checks | Low—pinned actions, secret scanning tools |
| Impact on ROI | Potential losses from breaches and downtime | Enhanced security boosts efficiency and trust |
| Implementation Cost | Low initial, high hidden (remediation) | Moderate upfront, long-term savings |
Conclusion: Secure Your Pipelines Today
John: In summary, exposed PATs are a stark reminder that GitHub Actions’ convenience comes with risks—but with OIDC, scanning, and best practices, you can safeguard your cloud. Prioritize this for ROI protection. Start automating securely with Make.com.
Lila: Don’t wait for a breach—act now, and keep building safely.

👨💻 Author: SnowJon (Web3 & AI Practitioner / Investor)
A researcher who leverages knowledge gained from the University of Tokyo Blockchain Innovation Program to share practical insights on Web3 and AI technologies. While working as a salaried professional, he operates 8 blog media outlets, 9 YouTube channels, and over 10 social media accounts, while actively investing in cryptocurrency and AI projects.
His motto is to translate complex technologies into forms that anyone can use, fusing academic knowledge with practical experience.
*This article utilizes AI for drafting and structuring, but all technical verification and final editing are performed by the human author.
🛑 Disclaimer
This article contains affiliate links. Tools mentioned are based on current information. Use at your own discretion.
▼ Recommended AI Tools
References & Further Reading
- GitHub Action Secrets aren’t secret anymore: exposed PATs now a direct path into cloud environments | InfoWorld
- Code to Cloud Attacks: Github PAT to Cloud Control Plane | Wiz Blog
- GitHub Actions Security: A Guide to Common Risks | Orca Security
- Over 10,000 Docker Hub images found leaking credentials, auth keys
- Flare Finds 10,000 Docker Hub Images Exposing Sensitive Secrets | eSecurity Planet
